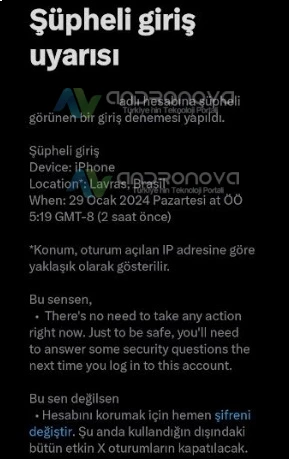
X şüpheli giriş uyarısı @…. adlı hesabına şüpheli görünen bir giriş denemesi yapıldı. Uyarı metninde ilgili konum, oturum açılan IP adresine göre yaklaşık olarak gösterilmekte olduğu vurgulanmakta. Hesaba giriş yapılan ülke, tarih saat ve kullanılan cihaz yazılmakta. Burada net olmayan genelde bölge olmakta.
X Şüpheli Giriş Uyarısı: Hesabına Şüpheli Giriş Denemesi Yapıldı
Güvenlik, çevrimiçi hesaplarımızın önemli bir parçasıdır ve çeşitli platformlar tarafından kullanıcılara sunulan şüpheli giriş uyarıları, hesap güvenliği için kritik öneme sahiptir. Bu tür bir uyarı almanız durumunda, ne anlama geldiğini anlamak ve doğru adımları atmak önemlidir.
Uyarının Anlamı ve Nedenleri:
- Şüpheli Giriş Denemesi: “X Şüpheli Giriş Uyarısı” veya benzeri bir bildirim almanız, hesabınıza birisinin yetkisiz bir şekilde giriş yapmaya çalıştığını veya giriş yapmaya çalışan bir cihazın tanımlanamadığını gösterir.
- Güvenlik Nedenleri: Bu tür uyarılar, platformların güvenlik önlemlerinin bir parçasıdır ve kullanıcıların hesaplarına yetkisiz erişim girişimleri olduğunda bilgilendirilmesini sağlar. Bu, hesabınızın güvenliğini korumak için önemli bir adımdır.
Ne Yapmalısınız:
- Uyarıyı Dikkate Alın: Uyarı aldığınızda panik yapmayın, ancak ciddiye alın ve hesabınızın güvenliğini sağlamak için hemen harekete geçin.
- Şifrenizi Değiştirin: Eğer mümkünse, hesabınıza hemen giriş yapın ve şifrenizi değiştirin. Güçlü ve benzersiz bir şifre seçerek hesabınızı daha güvenli hale getirin.
- İkinci Doğrulama Adımı: Eğer kullanıyorsanız, hesabınıza ikinci bir doğrulama adımı ekleyin. Bu, hesabınıza giriş yapmak için ek bir güvenlik katmanı sağlar.
- Platform ile İletişime Geçin: Uyarı aldığınız platformun müşteri destek ekibiyle iletişime geçin. Durumu bildirin ve gerekli adımları atmalarını isteyin.
- Diğer Hesaplarınızı Kontrol Edin: Şüpheli bir giriş denemesi yaşadıysanız, diğer çevrimiçi hesaplarınızın güvenliğini kontrol edin ve gerektiğinde şifrelerinizi değiştirin.
X Şüpheli Giriş Uyarısı İçin İlk Atılacak Adımlar
Uyarıyı aldıysanız hemen hesabınızın şifresini değiştirin ve ek giriş seçeneklerini kontrol edin. İki faktörlü doğrulamalı yöntemleri kullanın. X Premium için telefonla doğrulama, normal kullanıcılar için iki aşamalı kullanılabilir. Bunun için telefonunuza “Authenticator” uygulamasını kurun ve hesabınızdan doğrulama yapın. Sonrasında hesabınızda herhangi bir değişiklik yapılmış mı diye kontrol edin.
X İki Faktörlü Kimlik Doğrulamasını Açma
Ayarlar ve Destek başlığından “Ayarlar ve gizlilik” alanına geçin.
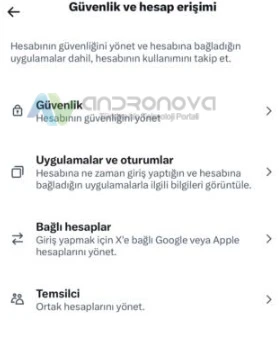
“Güvenlik ve hesap erişimi” kısmına geçin.
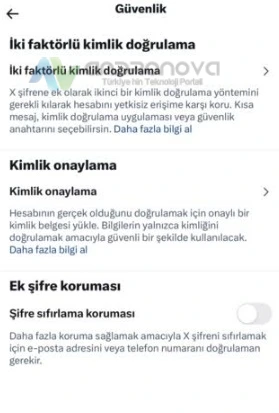
Güvenlik başlığına dokunun ve “İki faktörlü kimlik doğrulama” seçeneğine dokunun.
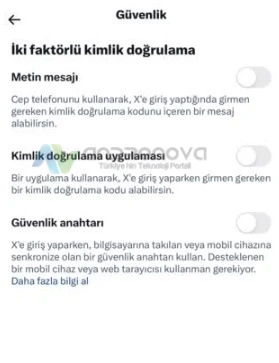
Son olarak, “Kimlik doğrulama uygulaması” adlı seçeneği açın.
Hesap Güvenliğine Yönelik Öneriler
1. İki Faktörlü Kimlik Doğrulama (2FA) Kullanın:
İki faktörlü kimlik doğrulama, hesaplarınıza giriş yaparken kullanıcı adı ve şifrenize ek olarak başka bir doğrulama adımı gerektirir. Bu genellikle bir SMS kodu, doğrulama uygulaması veya fiziksel bir güvenlik anahtarı olabilir. 2FA kullanmak, hesabınızın güvenliğini artırmanın etkili bir yoludur.
2. Güçlü Şifreler Kullanın:
Her hesap için benzersiz, karmaşık ve güçlü şifreler kullanın. Şifrelerinizde büyük ve küçük harfler, rakamlar ve özel karakterler bulunmalıdır. Şifre yöneticisi kullanarak güçlü şifreler oluşturabilir ve yönetebilirsiniz.
3. Düzenli Şifre Değişiklikleri:
Şifrelerinizi düzenli aralıklarla değiştirin. Bu, hesap güvenliğinizi artırmak için önemli bir adımdır. Özellikle hassas hesaplar için (banka, e-posta vb.) sık sık şifre değişikliği yapmak daha güvenlidir.
4. Hesapları Bağlama ve Yetkilendirmeyi Sınırlandırın:
Üçüncü taraf uygulamalarla hesaplarınızı bağlarken dikkatli olun ve sadece güvendiğiniz ve tanıdığınız uygulamalara izin verin. Gereksiz uygulama erişimlerini ve yetkilendirmeleri kaldırın.
5. Güvenli Bağlantılar Kullanın:
Hassas bilgileri paylaşırken ve giriş yaparken her zaman güvenli bağlantılar kullanın. Tarayıcınızın adres çubuğunda “https://” ve bir kilit simgesi olduğundan emin olun.
6. Cihaz Güvenliğini Sağlayın:
Cihazlarınızın güvenliğini sağlamak için yazılım güncellemelerini düzenli olarak yapın ve güvenilir bir antivirüs programı kullanın. Ayrıca cihazlarınıza parola veya biyometrik kilitleme ekleyerek fiziksel erişimi kısıtlayın.
7. Şüpheli Etkinlikleri İzleyin ve Bildirin:
Hesaplarınızda şüpheli etkinlikler fark ederseniz hemen şifrenizi değiştirin ve platform sağlayıcısına bildirin. Şüpheli e-postaları, mesajları ve bağlantıları açmayın ve bilgi güvenliğinizi korumak için dikkatli olun.
8. Bilinçli Olun ve Eğitim Alın:
Çevrimiçi güvenlik konusunda bilgili olun ve güncel tehditler hakkında bilgi edinin. Güvenlikle ilgili güncellemeleri takip edin ve düzenli olarak güvenlik eğitimleri alın.
X’ de IP Konum Bilgisi: Kullanıcı Gizliliği
X kullanıcıların gizliliği ve güvenliği önemli bir konudur ve X, kullanıcıların kişisel bilgilerinin gizliliğini korumak için çeşitli adımlar atmakta. Ancak, az çok X kullanıcılarının IP adresleri hakkında bazı bilgiler toplanabiliyor ve sonrasında kullanılabiliyor.
1. IP Adresi Nedir?
IP adresi, bir cihazın internete bağlandığı ağdaki benzersiz tanımlayıcı numaradır. Her cihazın kendine özgü bir IP adresi vardır ve bu adres, cihazın coğrafi konumunu belirlemeye yardımcı olabilir.
2. X’ de IP Konum Bilgisi Kullanımı:
Twitter, kullanıcıların IP adreslerini kullanarak coğrafi konumları hakkında bazı bilgiler toplayabilir. Bu bilgiler, kullanıcı deneyimini kişiselleştirmek, yerel içerik sağlamak ve güvenlik amacıyla kullanılabilir.
3. IP Adresinin Gizliliği:
X, kullanıcıların gizliliğini korumak için çaba sarf eder ve IP adreslerini genellikle kullanıcıların izni olmadan açıklamaz. Ancak, yasal yükümlülükler veya güvenlik nedenleriyle, Twitter’ın belirli durumlarda IP adreslerini ifşa etme hakkı olabilir.
4. Kullanıcı Kontrolü:
X kullanıcıları, hesap ayarlarında gizlilik ve güvenlik tercihlerini yönetebilirler. Bu ayarlar aracılığıyla kullanıcılar, IP konum bilgilerinin nasıl kullanıldığını ve paylaşıldığını kontrol edebilirler.
5. İP Konum Bilgisi ve Güvenlik:
IP adresleri, hesap güvenliği ve sahtekarlık tespiti gibi güvenlik amaçları için de kullanılabilir. X, kullanıcıların hesaplarının güvenliğini sağlamak için IP adreslerini izleyebilir ve anormal etkinlikleri tespit etmek için kullanabilir.
6. Kullanıcı Bilinçlendirme:
X, kullanıcılarına gizlilik ve güvenlik konularında bilgi sağlamak ve farkındalık oluşturmak için çeşitli kaynaklar sunar. Kullanıcılar, X’ın gizlilik politikalarını ve güvenlik uygulamalarını inceleyerek kendilerini korumak için önlemler alabilirler.
X şüpheli giriş uyarısı: Hesabına şüpheli görünen bir giriş denemesi yapıldı için neler yapılmalı adım adım anlattık.
Sonraki: X Hesabın Askıya Alındı





